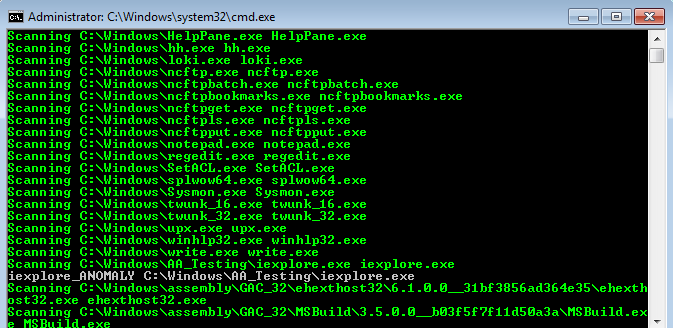
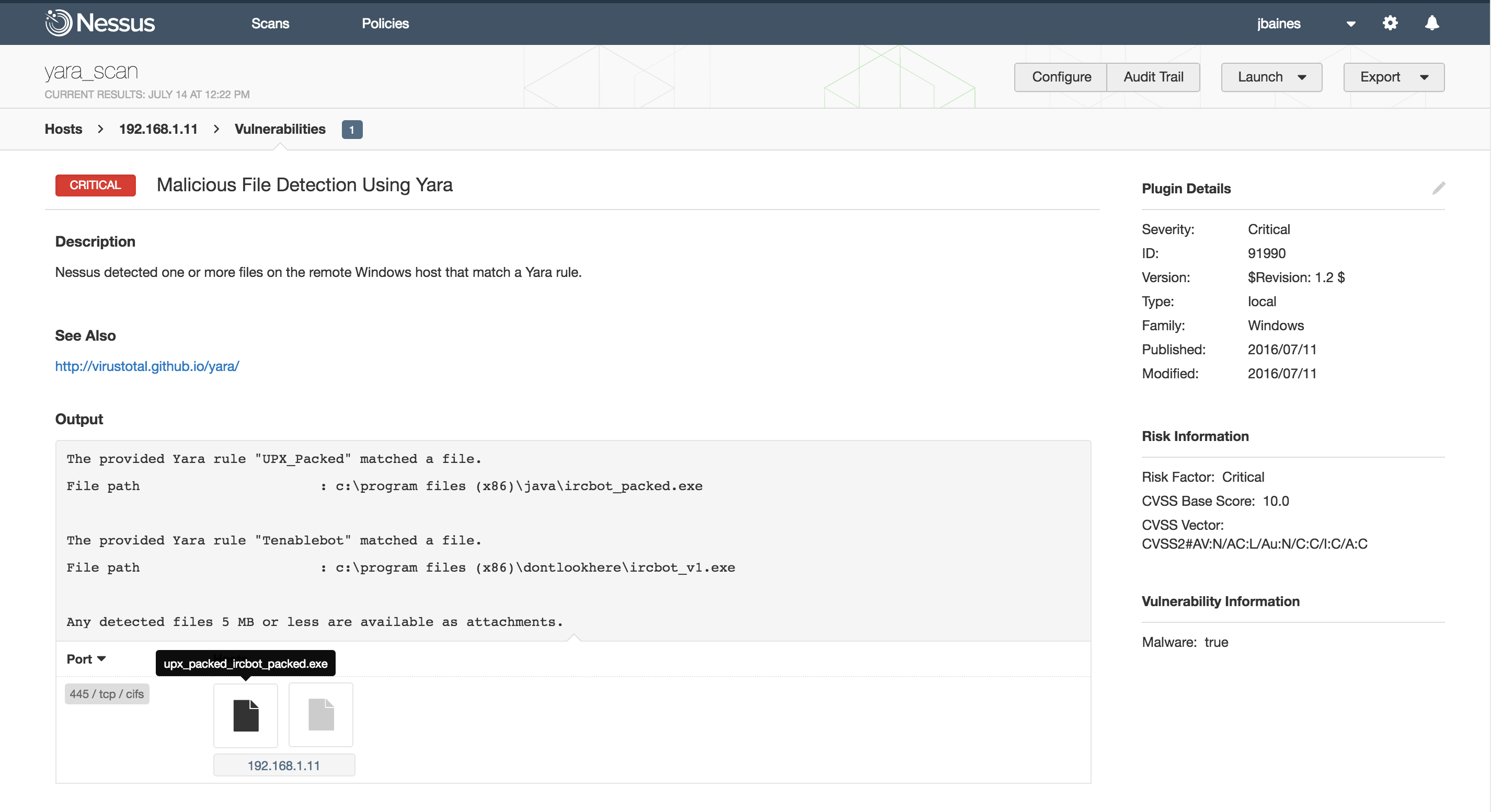
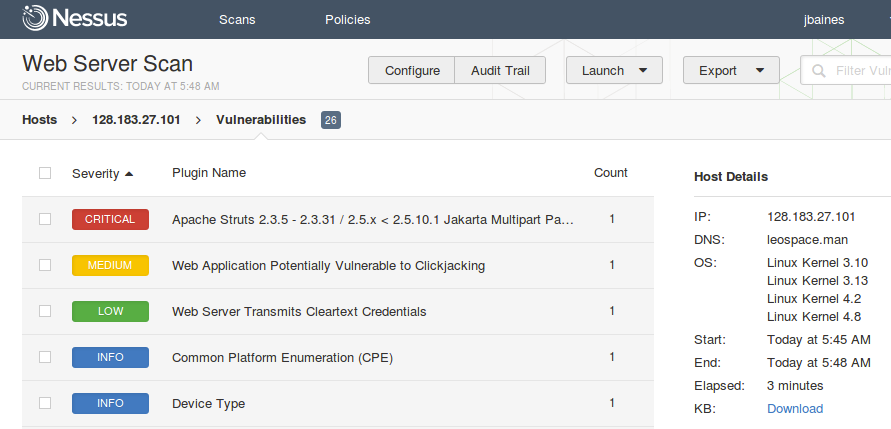
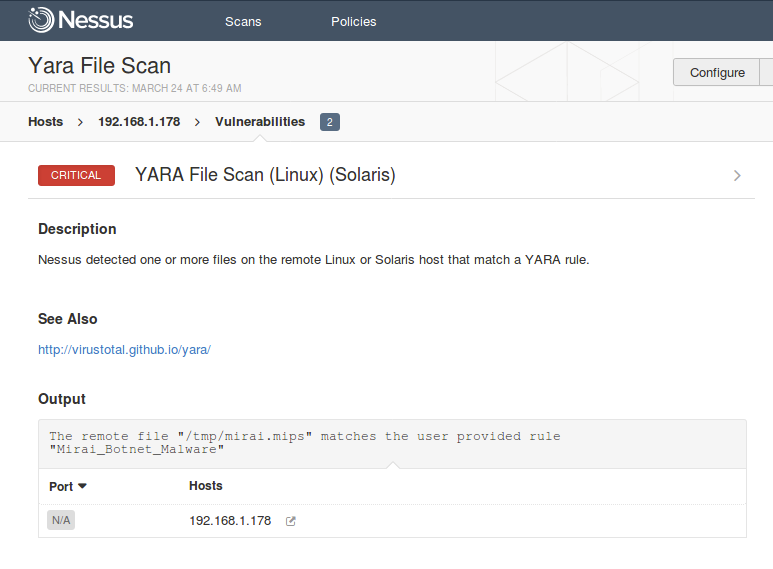
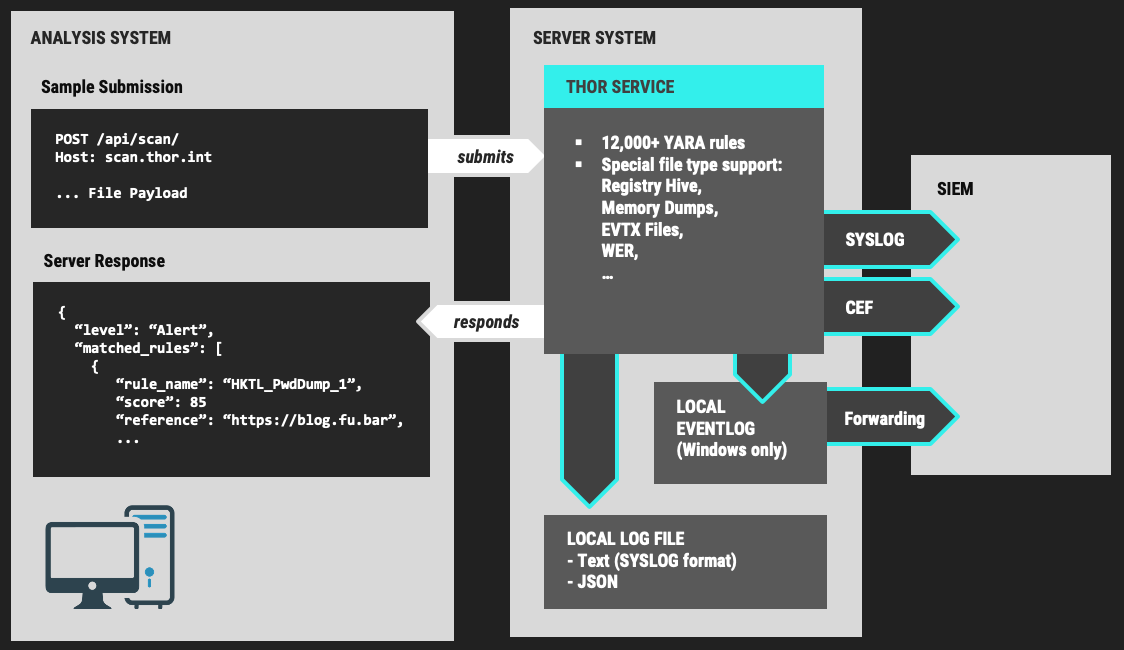
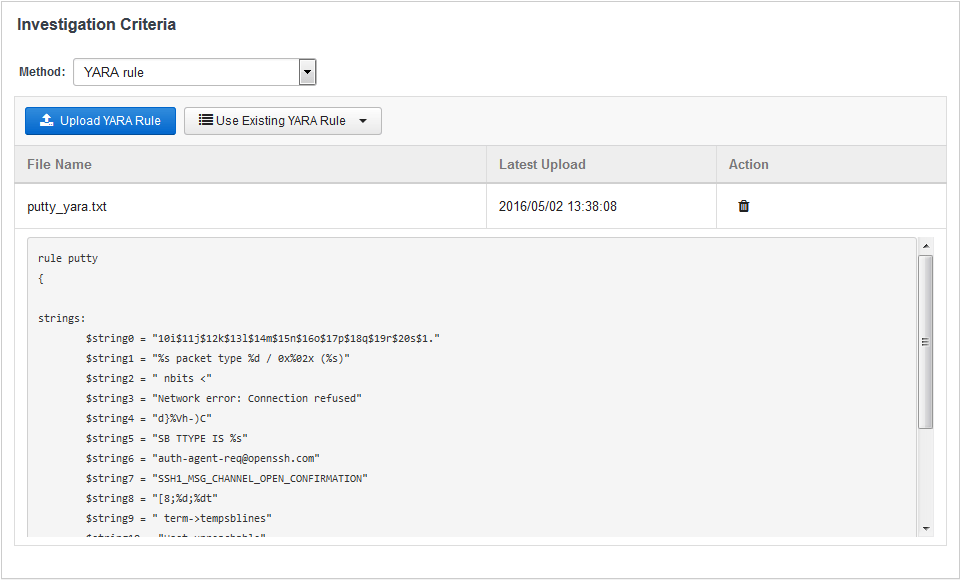
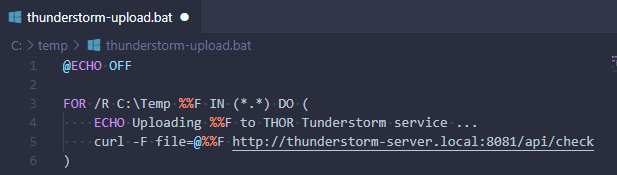
Nextron Systems on Twitter: "THOR Thunderstorm ⚡️ - An ultra-fast on-premise YARA scan service - Collect samples from inaccessible systems (ICS, IOT, embedded devices, network appliances etc.) - Get coverage for legacy
RSA NetWitness Endpoint error message: Unexpected condition while processing modules to post to serv... - NetWitness Community - 5588