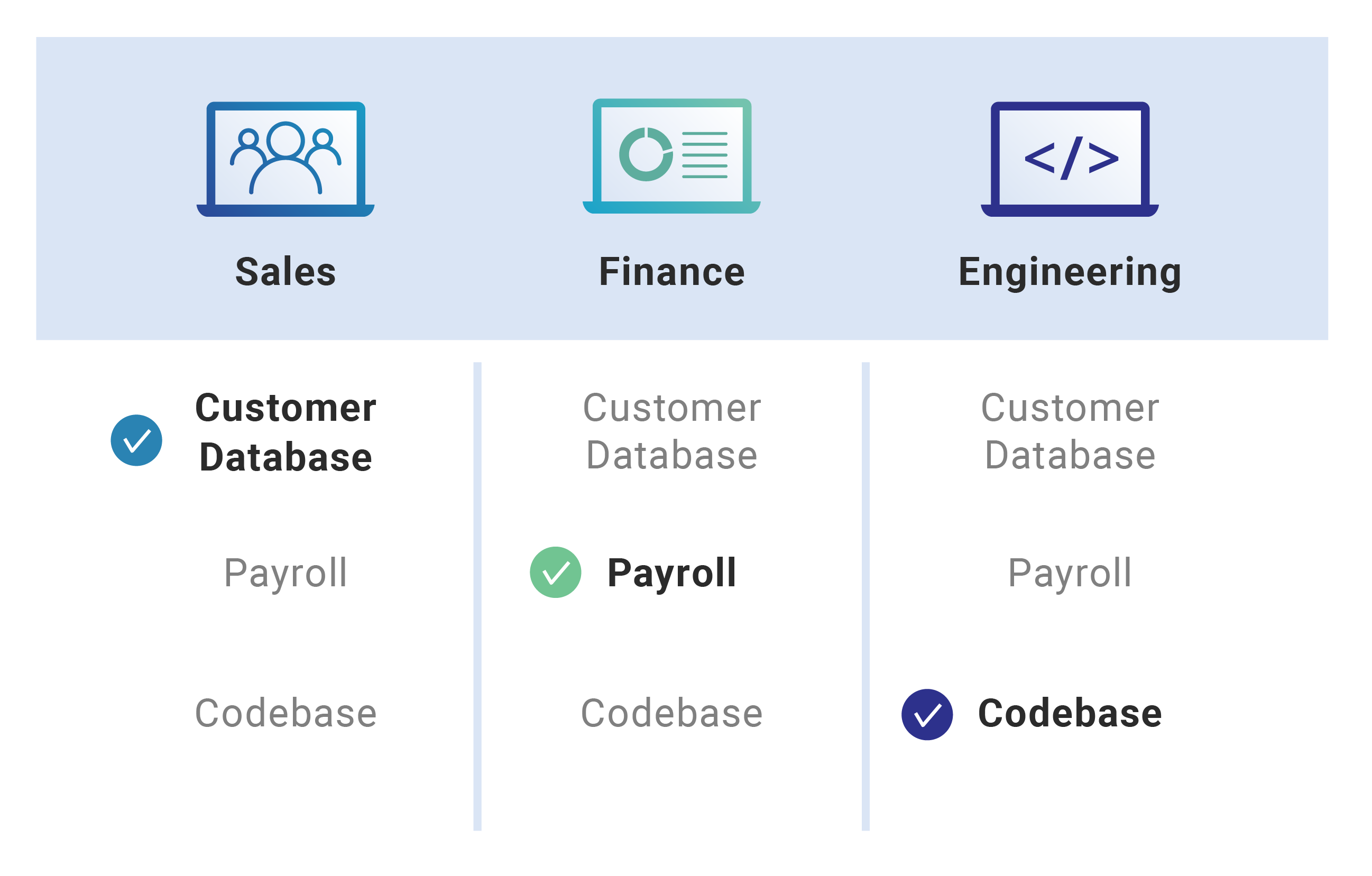
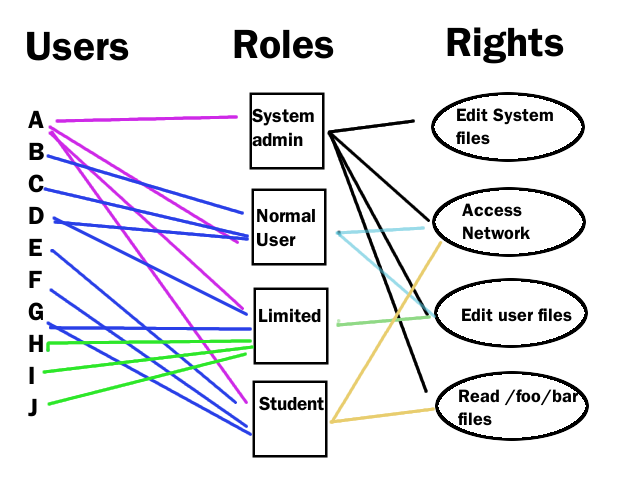
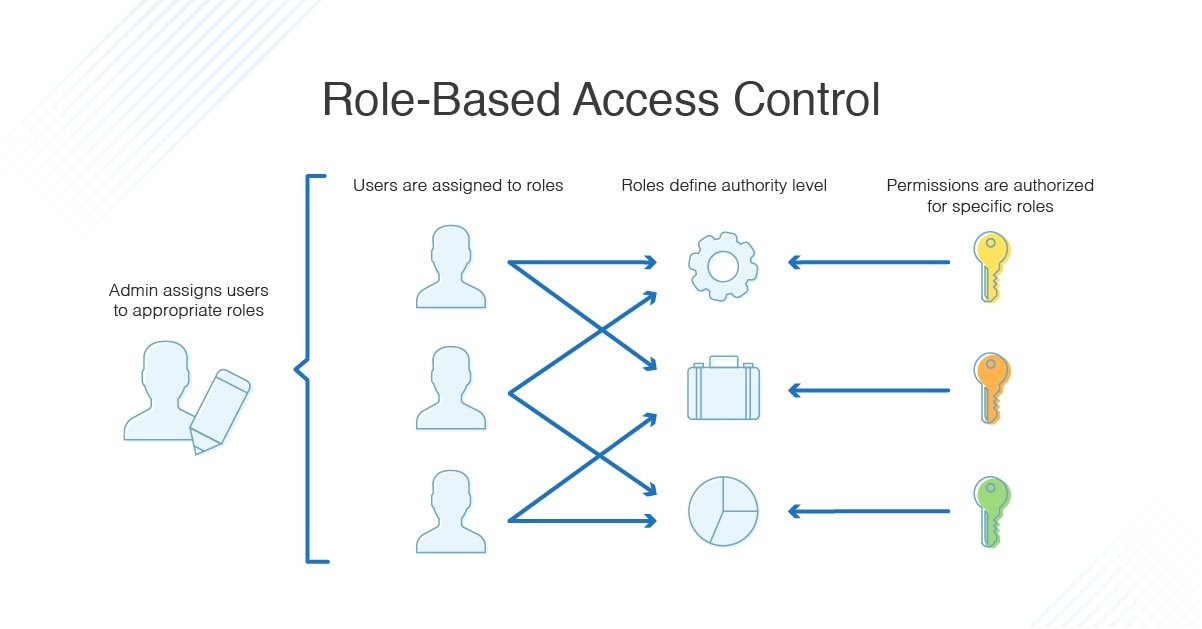
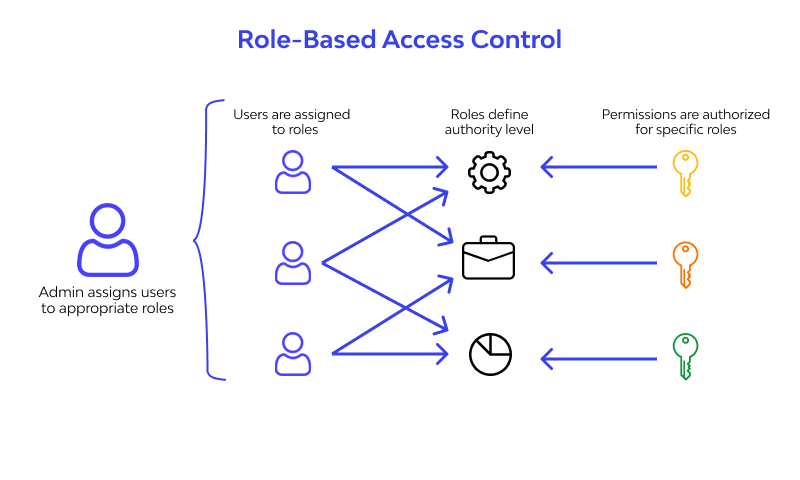
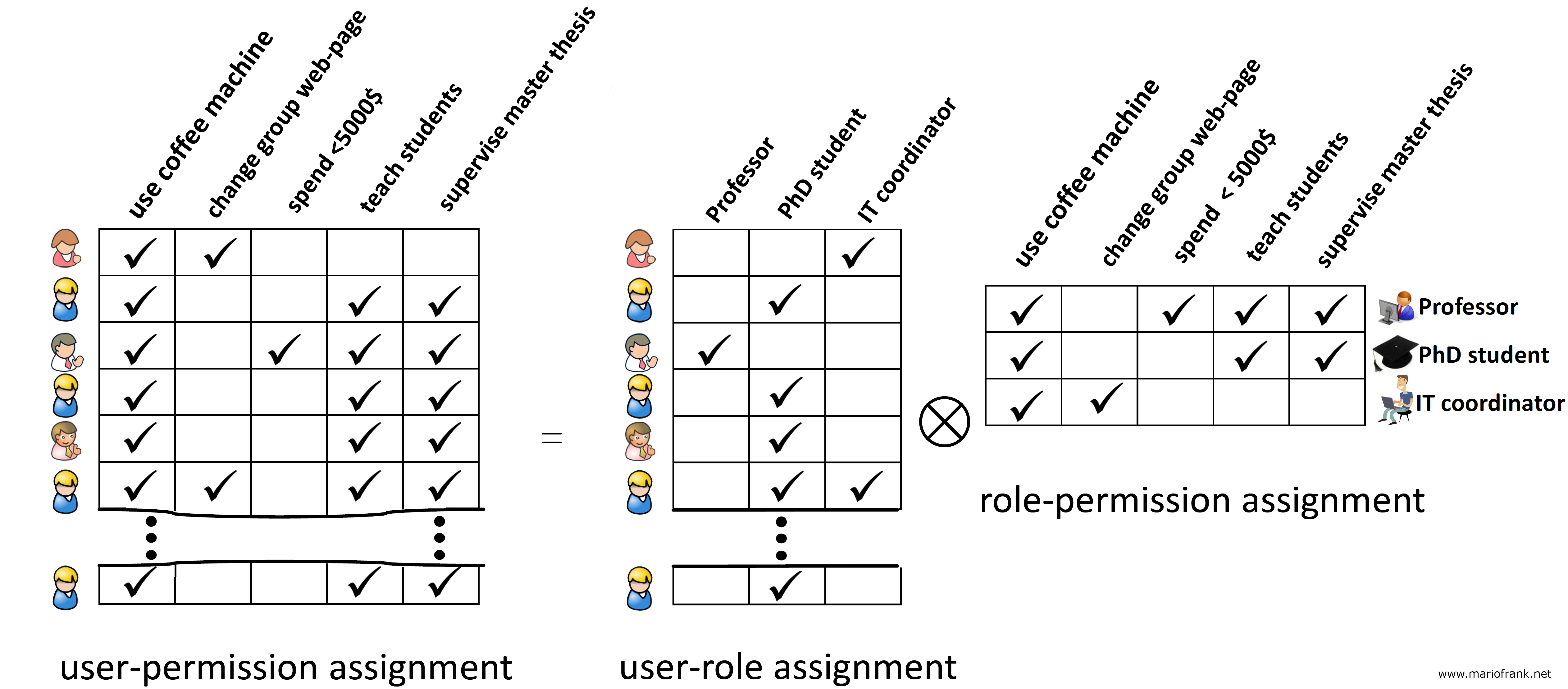
An enhancement of the Role-Based Access Control model to facilitate information access management in context of team collaboration and workflow - ScienceDirect

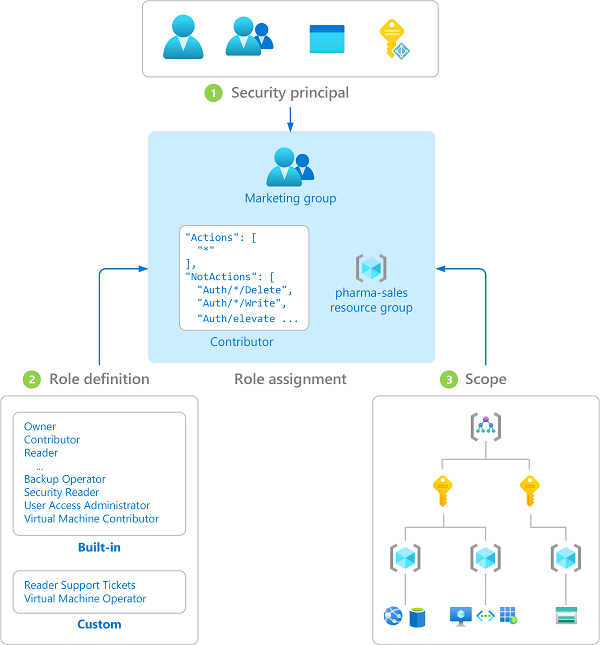
Role Based Access Control (RBAC) with Spring Boot and JWT | by Imesha Sudasingha | Geek Culture | Medium