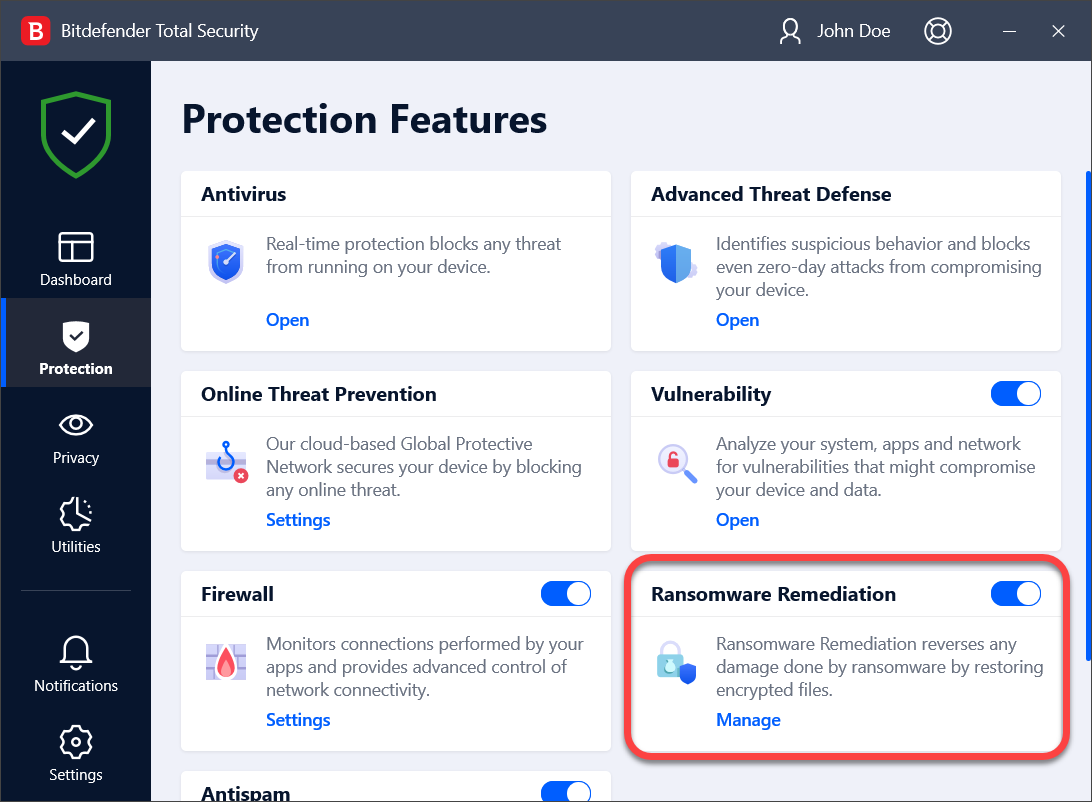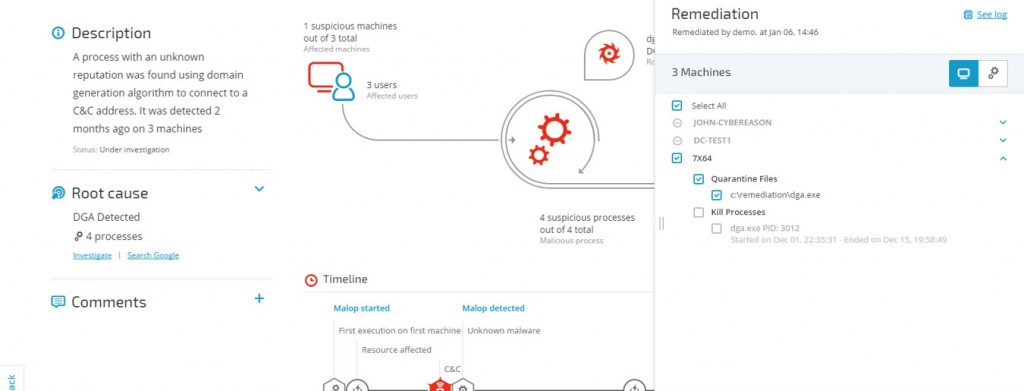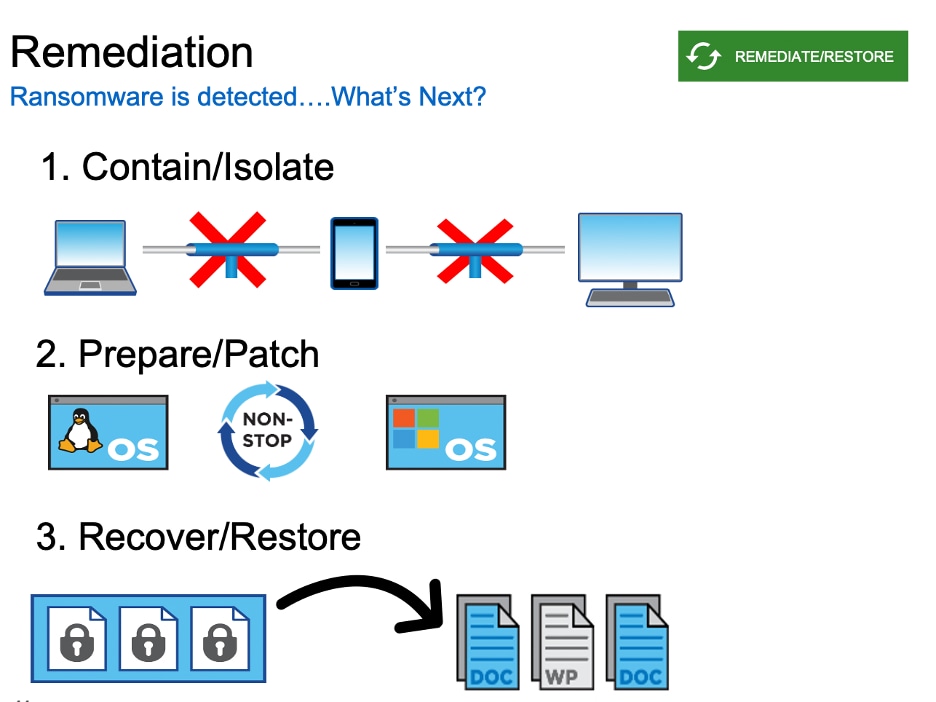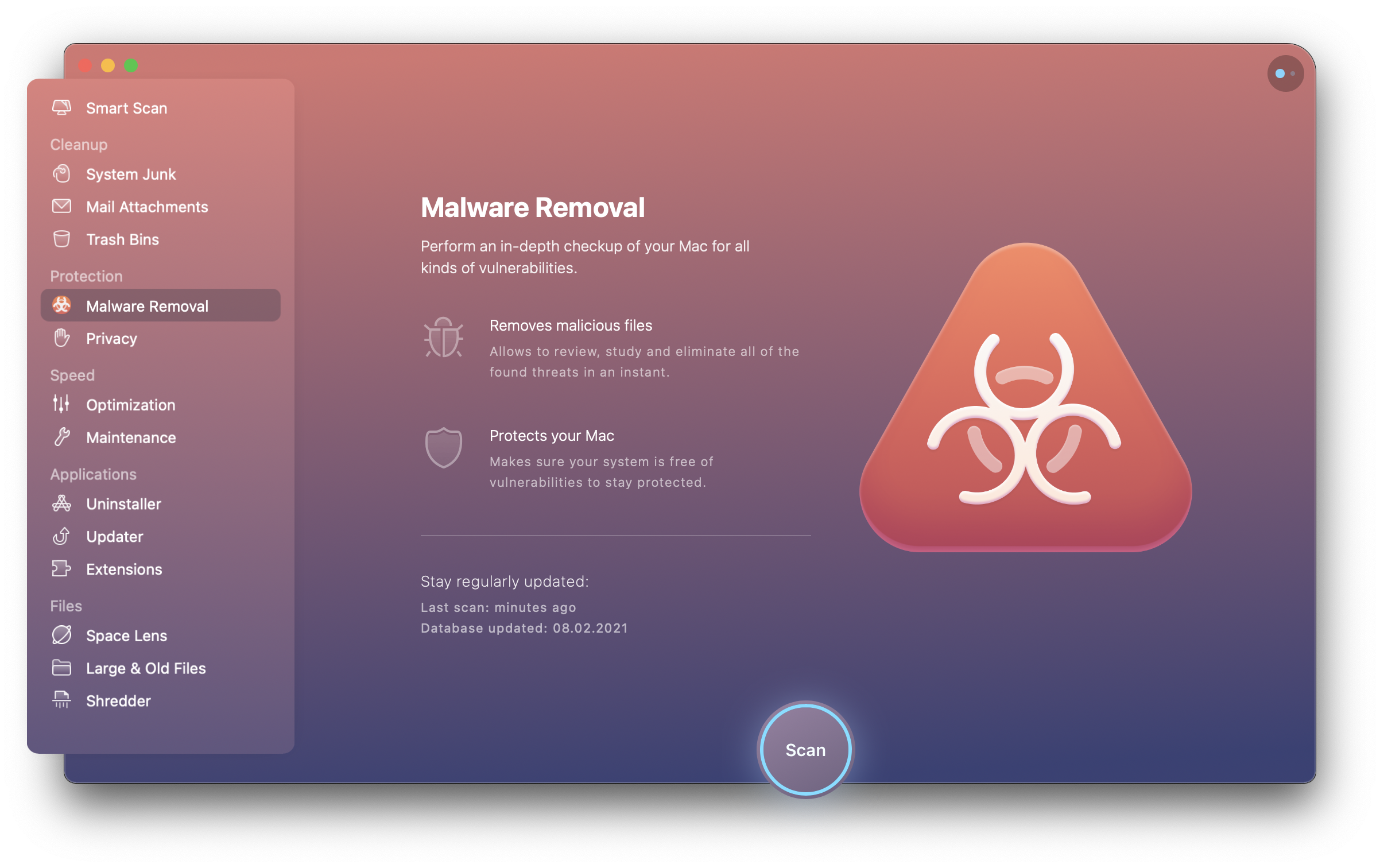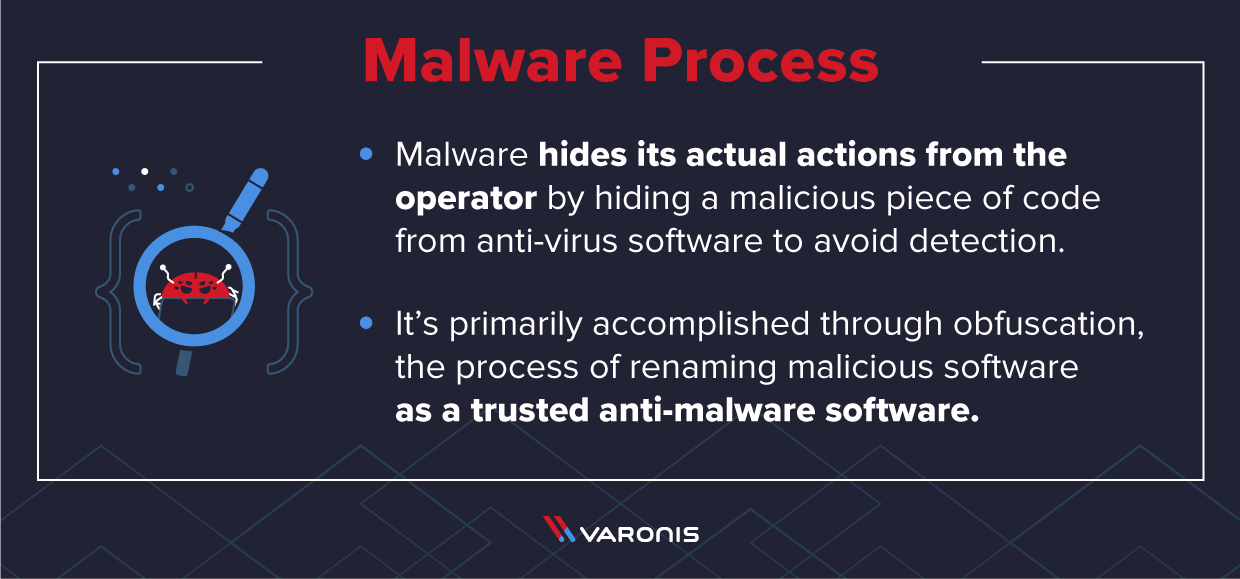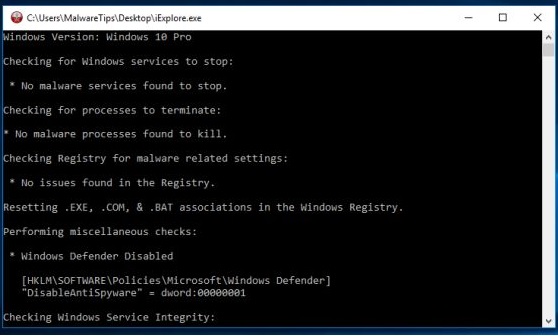
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology
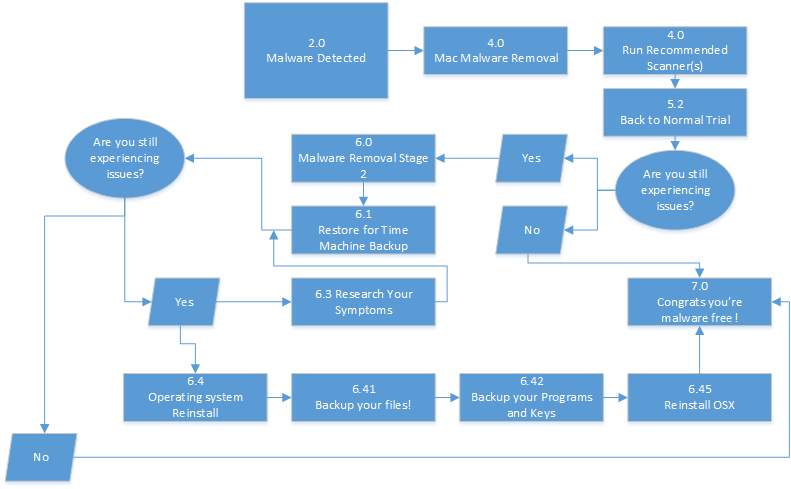
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology

8 Critical steps to take after a ransomware attack: Ransomware response guide for businesses - Emsisoft | Security Blog

SISA a Twitter: "Beware of #netwalker. #SISAInfographics highlights its attack pattern and remediation steps. #Infographics #Cybersecurity # Ransomware #Cyberattacks #NetworkSecurity #incident #incidentresponse #Hunter #CyberAttack #dataprotection #Data ...
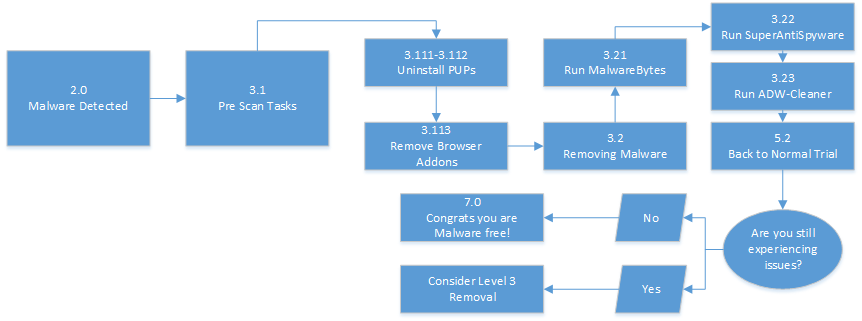
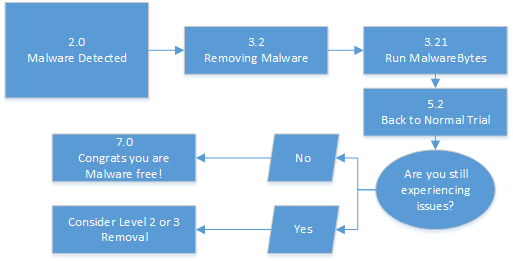
I've Got Malware, Now What? A Guide on Malware and Malware Removal | CAES Office of Information Technology




![How To Remove Malware From WordPress Site 2022 [Updated] How To Remove Malware From WordPress Site 2022 [Updated]](https://i0.wp.com/secure.wphackedhelp.com/blog/wp-content/uploads/2018/12/wordpress-malware-cleanup-steps-infographic.jpg?resize=574%2C2577&ssl=1)