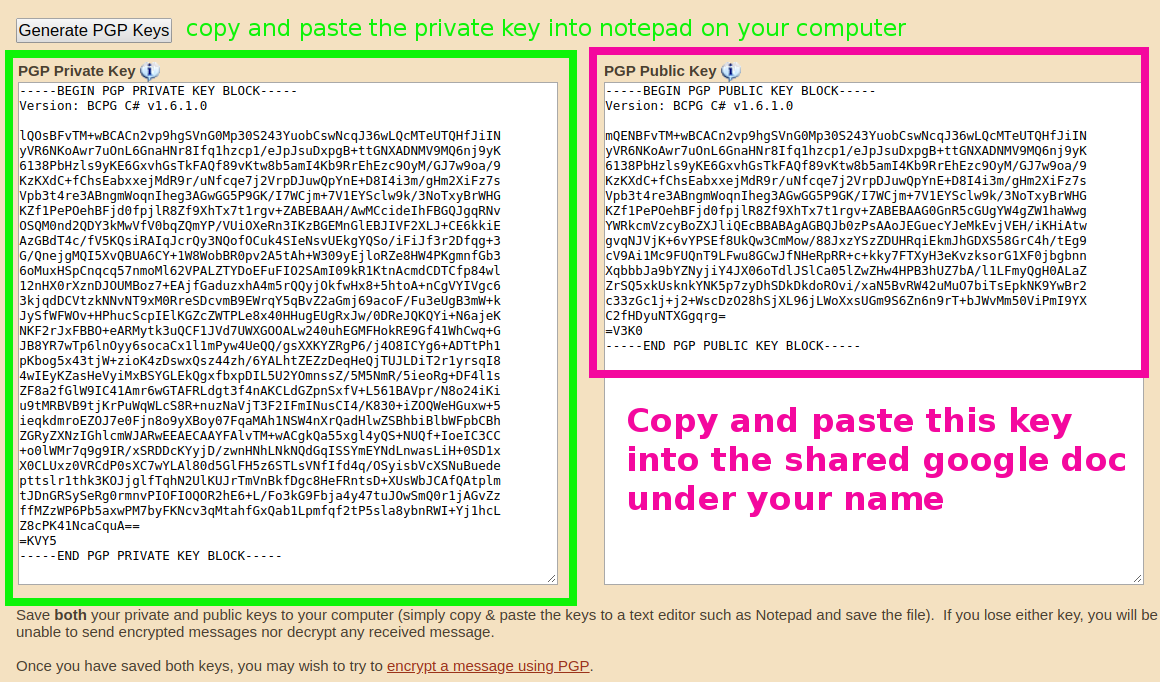
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense

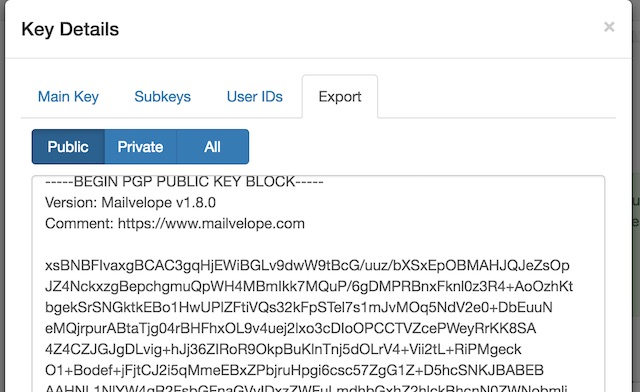
Why is GnuPG changing first two characters of ascii armored public key after downloading it from the key server? - Cryptography Stack Exchange

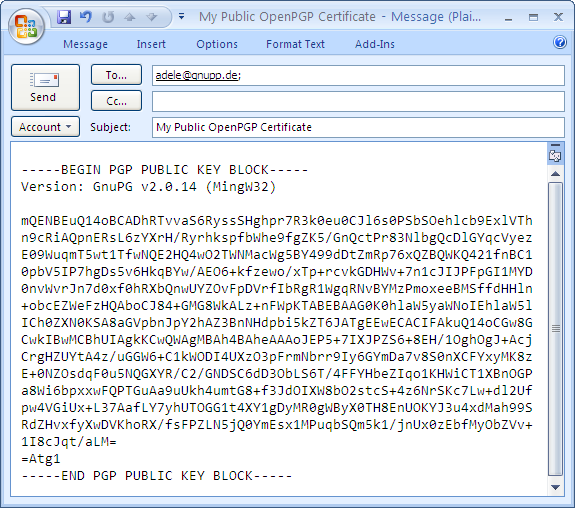
Email Encryption with PGP | How do I | Security Guidance | Security | Information Services | DePaul University, Chicago


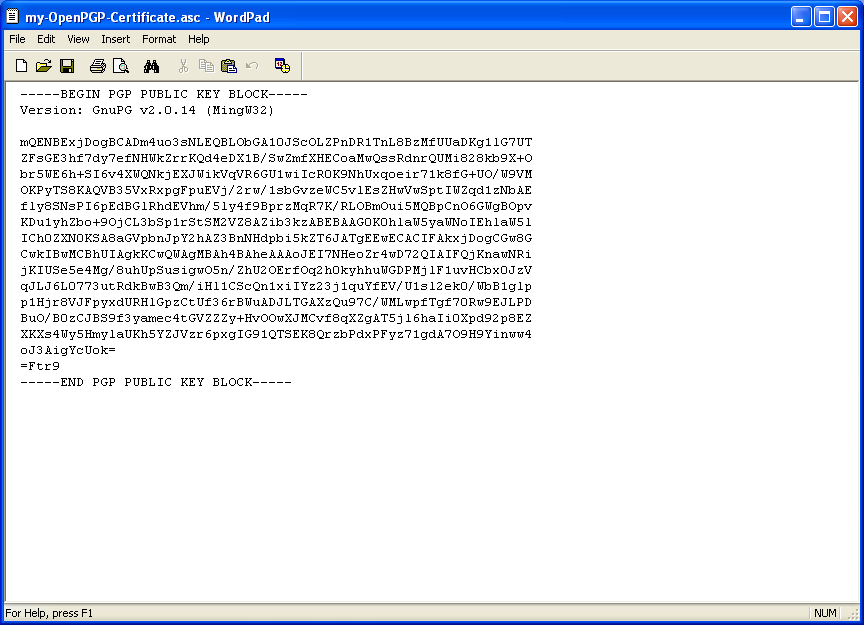
![A Noobs PGP Guide using Gpg4Win [Easy 5 Min Setup] - Deep Web A Noobs PGP Guide using Gpg4Win [Easy 5 Min Setup] - Deep Web](https://img.deepweb-sites.com/wp-content/uploads/2017/04/gJK0c9S1.png)